How Relay Works
Written by Russo • Updated: July 2025
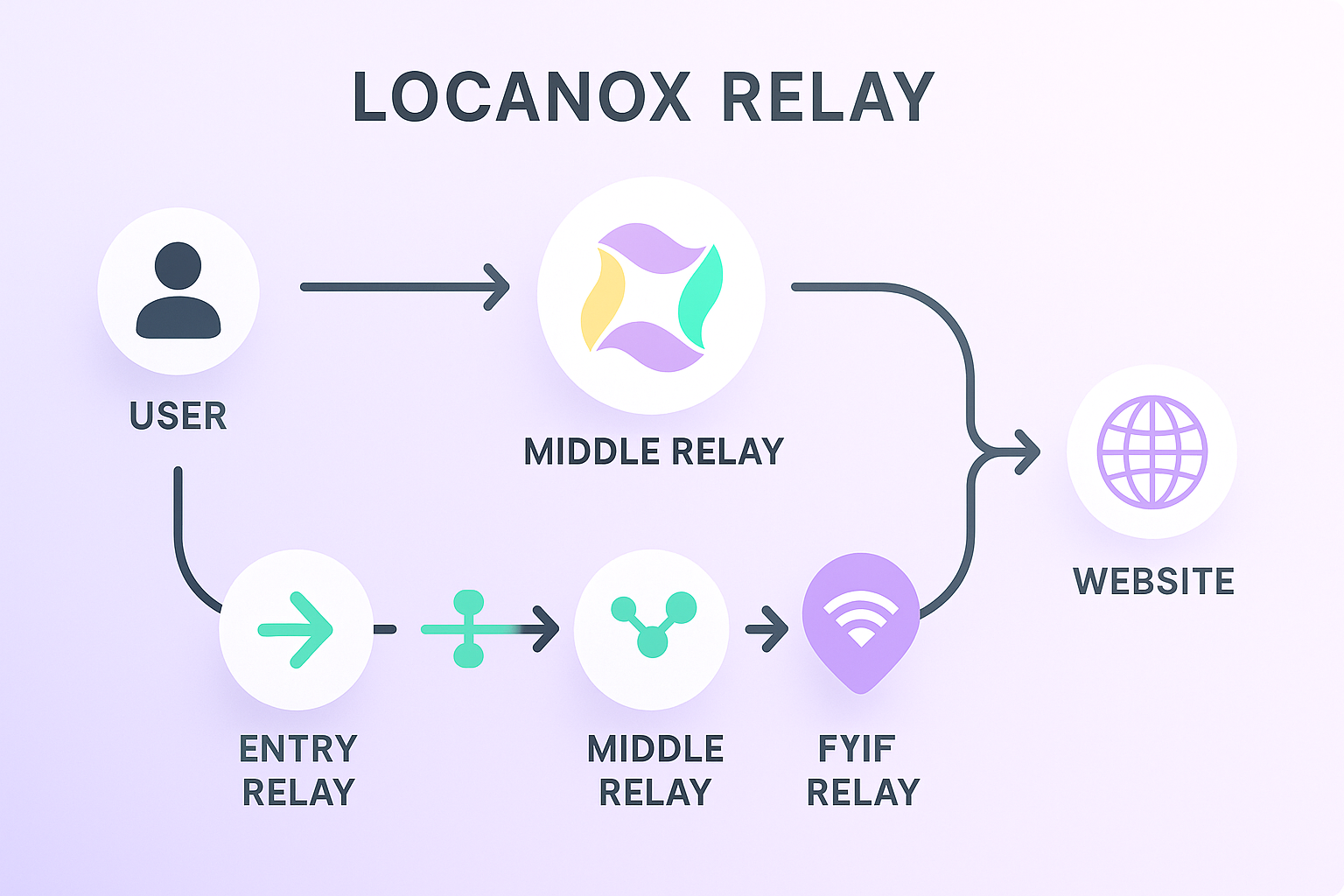
Locanox uses a custom relay network to enable online features without compromising your privacy. Instead of connecting directly to external endpoints, your requests are routed through ephemeral, encrypted relays, removing all traces of IP address, device metadata, or user identity.
These relays are stateless and randomized per session. When activated, each connection is wrapped in end-to-end encryption and masked by obfuscation layers that prevent external tracking. No connection logs are stored, and relays are rotated regularly to ensure unlinkability.
Relay channels are used for AI data fetches, IPFS uploads, encrypted messaging, and decentralized app interactions. Each relay only knows the next destination, never the source. This ensures your activity is never traceable back to your device.
✅ Relay Principles
Randomized routing nodes per session
Each online session uses a different combination of relay nodes for maximum privacy.
IP address is never revealed to destination
Your real IP address remains hidden from all external services and endpoints.
End-to-end encrypted tunnels
All data transmission is encrypted from your device to the final destination.
No logging or relay reuse
Relays are stateless and don’t store any connection logs or session information.
Only used in Private Online Mode
Relay networks are activated only when you explicitly enable online connectivity.
Disconnect = full session wipe
When you go offline, all relay connections are terminated and session data is cleared.
How the Relay Chain Works
The relay system operates through these layers:
- Entry Relay: Your device connects to the first relay node with encrypted traffic
- Middle Relays: Traffic is passed through additional relay nodes for obfuscation
- Exit Relay: The final relay node connects to the destination service
- Onion Routing: Each relay only knows the previous and next node in the chain
- Session Isolation: Each connection uses a fresh relay path with no reuse
This multi-layer approach ensures that no single relay can identify both your device and your destination, providing strong anonymity guarantees for all online activities.